Zero Trust in the SAP World


Cyberattacks in Germany are on the rise as digital networking continues. While large companies are well protected, small and medium-sized enterprises often offer easy gateways for phishing, social engineering, malicious code, malware, ransomware and DDoS attacks.
According to police crime statistics, more than 131,000 cases were reported last year. The ongoing trend is being boosted by the use of artificial intelligence. The technology lowers the barriers to entry for attackers and increases the scope, speed and impact of attacks.
Cloud vulnerability
Cloud solutions are a potential weak point in companies. They have long been considered trustworthy, but with the wrong security architecture, such as insecure networks, weak passwords, unencrypted data and loose permissions, they offer numerous opportunities for misuse. Another risk is posed by people themselves.
Many employees lack awareness, are insecure or careless when dealing with deceptively genuine-looking phishing emails or realistic-looking media content („deepfakes“). The question is often not whether a company will be attacked, but when - and then it should be as resilient as possible. In the current threat situation, traditional approaches are often reaching their limits. The trend towards remote work also means that traditional perimeter protection using firewalls and VPNs is no longer sufficient. Companies are therefore required to strategically realign their IT security to the requirements.
It is advisable to take a holistic view of the topic, i.e. to include the factors of people, processes, applications and data. Security concepts such as „Zero Trust“, protection at all levels - from data to identity - form the foundation. The model is based on the principle of minimal rights for all entities in the overall infrastructure. This means that no one is trusted „blindly“, but every access - whether from the internal network or from outside - is checked in real time.
Small network
Important elements in such an environment are a stable infrastructure, trustworthy devices and encrypted sensitive data, databases and data transfers. Systems should be regularly assessed, updated („patch“), secured („backup“) and recovery tested („recovery“) to fix bugs, close security gaps and improve performance and functionality. It is advisable to keep the network as small as possible, separate critical systems and use modern firewalls (layer 7) to monitor and control traffic.
The applications should be connected to a central identity provider that provides the user base for the applications. This is the only way to implement the „One Identity“ concept. The aim is to be able to log in to each application with a central identity. This makes it possible to implement technical processes that simplify logins through single sign-on (SSO) and secure them through multi-factor authentication (MFA).
Administrators receive access „just in time“ for a limited time and a limited area. This ensures that the right device with the right identity accesses an application in the right context. The result is not only more secure IT, but also a massive reduction in support and operating costs and easier administration.
Identity Authentication Services
How can Zero Trust be implemented technically and organizationally in the SAP world? In many companies, historically and heterogeneously grown landscapes consisting of SAP systems and non-SAP systems or applications such as Microsoft Office 365, Microsoft SharePoint and Microsoft Teams are the standard.
These applications often access different user databases and login mechanisms. This leads to different login masks, different password policies, distributed role concepts and silos in user management.
Central authentication
In order to create a more secure environment, it is essential to tidy up these areas. This also has an impact on the usability of business applications for every user, greater compliance through centralized authentication and consistent processes. A key step in implementing Zero Trust is choosing the right security architecture with an integrated launchpad. It acts as a central, overarching entry point for business applications, independent of individual systems and solutions.
A low-code tool that can create digital work environments according to these requirements is the SAP Build Work Zone Service provided on the SAP Business Technology Platform.
It offers secure, centralized, personalized and role-based access to SAP and external applications, processes and data. Content and functions are tailored to the user roles, i.e. users only see what they are allowed to see.
This enables a new way of dealing with the existing landscape. This also includes automated workflows and integrated communication tools.
SAP Work Zone Service
Content from different connected systems can be seamlessly integrated via the SAP Work Zone Service. This works for cloud solutions such as SAP SuccessFactors or SAP Analytics Cloud as well as via Cloud Connector for on-premises solutions such as SAP S/4 Hana, SAP BW, SAP HCM and SAP NetWeaver Portal. Interfaces and authorization concepts of already established roles can be easily reused via content federation. The unique and uniform authentication, including single sign-on, the exchange of login certificates and the like, is then controlled via the SAP Identity Authentication Service.
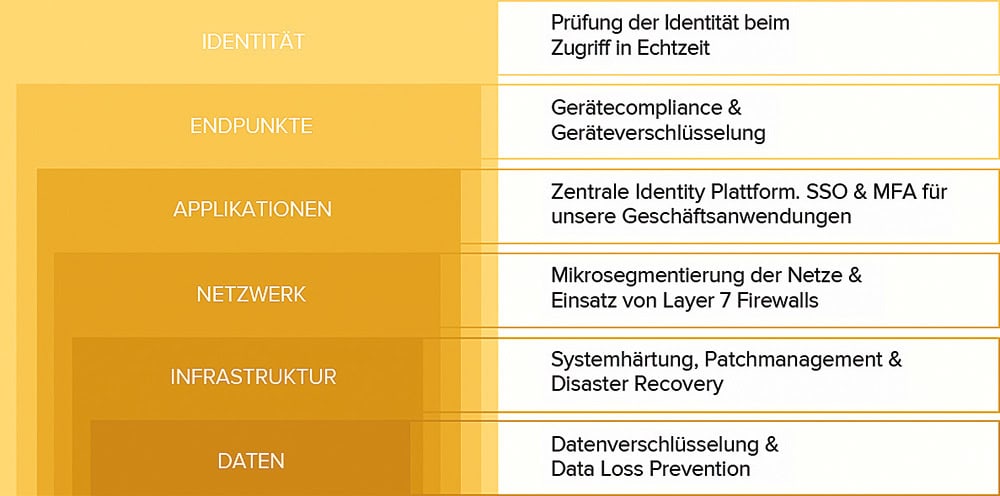
Zero Trust: protection at all levels - from data to identity.
One identity for all systems
If you do not want to control identity and access management on SAP BTP but centrally, for example with Microsoft Azure, you can connect Microsoft Entra ID as a corporate identity provider in SAP Identity Authentication Services. This allows the existing user base to be reused, and if the end devices are also connected to Microsoft Entra ID, it is also automatically recognized in the background whether the device used is trustworthy or not.
The advantage of all this is that users only have one overarching identity for user login, which they can use to log in to all connected systems. This greatly simplifies password guidelines and associated processes such as resetting.
SAP Identity Provisioning Services
To make identity and access management more user-friendly, SAP Identity Provisioning Services can be used to read user information and authorizations from a central system and automatically distribute them to connected systems. The identities and authorizations are created in the user administration to match the central truth. This reduces the effort involved in onboarding and offboarding, while at the same time reducing the susceptibility to errors caused by manual maintenance in the various systems. Zero Trust is more than just a security concept or a single tool - it is the future of modern, holistic IT security.
In view of the fast-moving cloud and AI world, it must be updated on an ongoing basis. Three steps are essential here: an inventory with analysis and conceptual design, the choice of architecture and the choice of services and licensing. The recommendations from the SAP reference architectures for licensing and documentation serve as a guide.
SAP Architecture Center
The SAP Architecture Center, where you can find suitable reference architectures for a wide range of technologies and services, is also a good place to start. Cloud Identity Services are a linchpin in modern (hybrid) SAP landscapes to ensure secure authentication across the various systems.





