Security and Compliance with SAP in the Azure Cloud
![[shutterstock.com: 786616078, Pasuwan]](https://e3mag.com/wp-content/uploads/2020/04/shutterstock_786616078-scaled-1200x800.jpg)

If you look at classic security frameworks, such as ISO 27001 or IT-Grundschutz, they all follow the three principles: Availability, confidentiality and integrity.
This means that the data and IT systems must be available and accessible, only those who are authorized may access them, and the data must not have been changed.
Microsoft is making enormous efforts to establish these principles at all levels and services in the Azure Cloud. The annual budget for security alone exceeds the $1 billion mark.
Let's make a comparison between traditional IT security and cloud security. The demands on IT security increase enormously every year, the cat-and-mouse game with the ever-increasing threat of ransomware as well as permanently changing regulatory requirements leads to a balancing of interests in the IT security budget between protection needs, costs and risk and the question:
Have I done everything and am I safe? The current prevailing opinion is that you cannot take enough IT measures and that it is therefore more important to focus on detection. This balancing act leads to a patchwork of measures, some of which have very different characteristics and levels of maturity and, taken together, may offer too little protection.
The large hyperscale cloud service providers have planned and implemented security down to the smallest cog. It would take several books to cover all the aspects that Microsoft undertakes to protect data. Security is by no means a black box that I simply have to trust without any checks and balances.
There are extensive audits and reports on this, which generate a great deal of transparency. We will come to this point later. We will focus here on the most important points and compare them with traditional IT operations: physical security in the data center; security design and operations; IT infrastructure protection; monitoring and logging; update management; anti-malware; and identity and user access management.

If I run a computer room today, I have to ask myself if I have thought of everything and considered all scenarios of power, cooling, building, etc. failure.
I have to constantly maintain the equipment, let technicians into my data center and do a risk assessment. Recently, this has also included a pandemic. The effort required to operate a data center properly and securely is constantly growing, because the need for protection and the importance of IT data are also increasing.
To enter a Microsoft data center, several levels of screening are required including full-body metal detection screening and additional personnel security screening. This procedure can take up to 45 minutes.
Perimeter security is built in several tiers, as if in onion skins, thereby ensuring that no unauthorized person is allowed to enter. Security personnel patrol regularly and seismic alarms and video cameras monitor the building.
Microsoft operates data centers in 58 regions worldwide, and each region has multiple data centers. This enables an availability of 99.9 percent as a minimum for a singular virtual machine, which in turn pays into the protection goal of availability. In the event of a disaster, the use of local and geo-redundancy means that SAP operation can always be ensured in all possible and impossible scenarios.
Security Design and Operations
An important operating principle that Microsoft follows in hardening its cloud services is to assume an intrusion. Already in the development of new services, a large part is invested in the design of preventive measures and thus security-by-design is directly pursued.
Prevention is very important, but it is only the beginning of an effective security strategy, so Microsoft assumes that attackers can get in. This makes it all the more important, in addition to prevention, to minimize the impact of the attack and detect it quickly, minimizing the response time for a countermeasure.
Security prevention strategies and technologies cannot guarantee defense against an attack. It is more likely that a company has already been compromised, but the attacker has not yet been detected. This means that the security strategy must change fundamentally accordingly and move more in the direction of attack detection.

Microsoft uses the concept of the "Red Team" (attack) and the "Blue Team" (defense) for this purpose. The Red Team is a group of Microsoft hackers focused on breaking into the Microsoft infrastructure and platform.
Targeted persistent attacks on the services are carried out. The blue team consists of the security organization, which is responsible for responding to security incidents and operates globally 24 by 7.
It detects attacks and fends them off, regardless of whether the attack was carried out by the red team or by a real attacker. This concept results in the security organization being permanently on alert and continuously training and improving.
Only very few customers have such in-depth monitoring measures in their data center operations, let alone a security response team that is also available around the clock and can react properly.
We often see a patchwork of applications and measures, but they don't work end-to-end. Implementing a Security Information and Event Management (SIEM) or an Intrusion Detection and Prevention System (IDS/IPS) does not mean that I am immediately safe.
The resulting logs must be systematically reviewed and evaluated, and the resulting measures must be re-implemented in metrics. This costs time and resources. Microsoft ensures this for the infrastructure layer.
Security monitoring
Since Microsoft is responsible for the underlying infrastructure and data centers, the customer should also subject its own servers and applications to the concept of continuous detection in the "shared responsibility" concept. For this purpose, Microsoft offers the three services Azure Monitor, Azure Security Center and Azure Sentinel.
Azure Monitor is the classic infrastructure monitoring that captures typical parameters such as CPU, RAM, disk, availability, network, etc. It is flexibly extensible and even offers SAP Hana integration, which allows monitoring the specific parameters of a database.
Azure Security Center gives you a centralized view of the security status of your assets and the security control configurations in place to protect them. This allows you to detect threats faster and respond more effectively. Rest APIs support integration with existing systems and diverse data pots can be collected and analyzed.
Azure Sentinel is a SIEM (Security Information and Event Management) that helps detect and prevent threats before damage is done. It correlates all logs from your IT landscape using AI-based algorithms to respond faster and smarter.
However, as important as perimeter protection and detection are, so are regular updates and patches. Microsoft offers the Azure Update Manager and Azure Automation for this purpose. Patches are a necessary evil that customers like to avoid because it involves effort and downtimes of the SAP systems.
Through Azure Automation, we were able to almost completely automate the update process on the Azure platform for both Suse Linux and Windows systems.
Even the starting and stopping of the SAP Basis stack and the database are integrated in this process and lead to reduced effort and downtimes. SAP patches currently remain manual, as the application is affected in some cases and there is no way to completely avoid tests and manual work.
Malware protection and DDoS
From the range of malware protection, I would like to pick out a very interesting service that adds real value to a massive threat scenario.
Azure Advanced Threat Protection (ATP) is a cloud-based security solution that uses Active Directory to identify, detect and investigate advanced threats, compromised identities and malicious insider actions targeting your organization. Based on AD logs, anomalies and malicious behavior can be detected and defended against early.
Azure has a defense system to protect against DDoS attacks on the Azure platform and services. The protection is designed to detect attacks generated from both outside and inside the platform.
Basic DDoS Protection is automatically enabled as part of the Azure platform. Azure DDoS Protection Basic Protection provides continuous traffic monitoring with near real-time detection of a DDoS attack without the need for intervention and prevents it.
Intelligent metrics learn customer landscape resources and configuration, as well as application patterns to avoid false alarms.
Identity Management
Identity is a critical layer for security. The trend is to view this as the primary perimeter for security. This is a shift from the traditional focus away from network security, as accesses become more porous, credentials need to be more finely and securely defined.
In general, Microsoft employees do not have access to customer data. In the case of support, the customer can decide whether or not an employee is granted access under supervision. This means that the customer has complete control over who is allowed to do what.
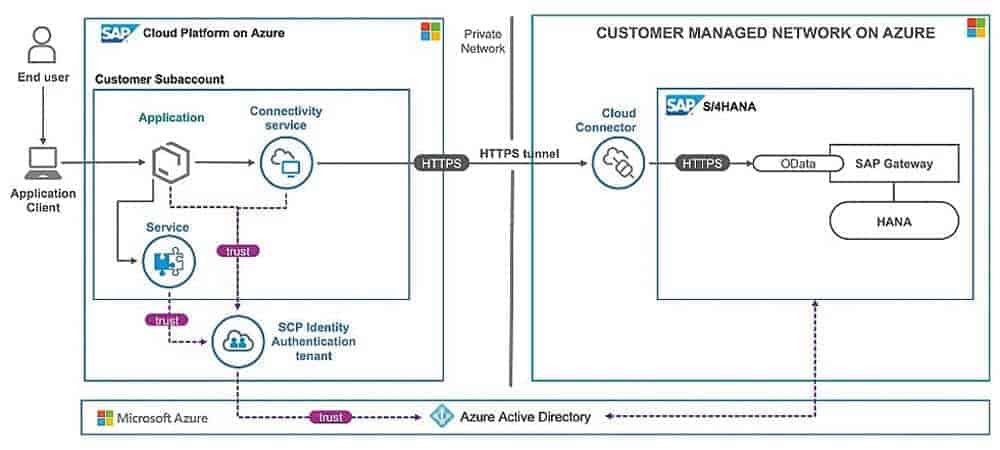
The strongest tool for enforcing roles and permissions is the well-known and proven Azure Active Directory. The linchpin of identity monitoring is the Azure AD, which is integrated and can be used in all Azure Services.
Azure-AD allows to protect identity, manage privileges, define and review access and establish global multi-factory authentication. Syncing with an on-premises AD is straightforward, enabling quick and easy integration and migration to the cloud.
With Role-Based-Access-Control (RBAC), authorizations can be defined very finely per service and assigned to employees according to their role. The built-in self-service password reset (SSPR) can reduce costs in 1st-level support.
Embrace
The Embrace program between Microsoft and SAP now makes it possible to set up user management and authenticate users almost seamlessly between the two worlds.
A single sign-on (SSO) with Azure-AD allows users to seamlessly jump from one application to another without interruption. This greatly increases protection and usability.
Azure Networking provides the infrastructure to securely connect virtual machines (VMs) to each other and to the outside world. By definition, each customer has their own private Azure cloud environment (subscription and tenant) that they can control.
Virtual networks can be created, routers set up, IP address ranges set and VPN connections and gateways switched. This involves logical separation from other customers and isolation of data.
There is a wide range of network services, such as load balancers or IDS/IPS services, which are also provided by 3rd party manufacturers such as Checkpoint or Cisco on the Azure platform. Thus, the customer can also find and use his familiar tools.
Generally, when network traffic leaves a location, it is encrypted and secured by Microsoft so that it cannot be accessed from outside. The classic site-to-site or client-to-site tunnel via IPsec/IKE VPN can be used to establish secure connections between the customer network and Azure. Express routers offer another option.
They are a private connection through which the customer's service providers switch a line directly to the respective Azure region, comparable to MPLS. Thus, bandwidth, latency and availability are guaranteed. Microsoft maintains many different peerings with the most common service providers.
Data is stored on Azure on different storage media that are always logically separated from other customers. Microsoft ensures that data is separate, encrypted, redundant, and securely destroyed when not in use.
By default, all data on all storage classes is always encrypted with AES-256. Especially for Blob and Azure files, customers can manage the key themselves using Azure Key Vault, a private key safe.
With standard Azure storage redundancy, the customer's data is always stored locally in a data center on three copies. This concept is called Locally-Redundant-Storage (LRS) and provides 99.99999999999 percent (eleven nines) availability of objects over a given year.
Zone Redundant Storage (ZRS) synchronously distributes data across three Azure Availability Zones (data centers) in a region. This means that availability can be increased to twelve nines after the decimal point. If this is not enough, you can have your data mirrored in another region (country), which is then called Geo-Redundant Storage (GRS).
Compliance
With over 90 compliance certifications, Microsoft has nearly every certification and industry requirement in its repertoire to meet customer and government requirements.
Let's take a closer look at the most important ones for the German market and SAP operations: The ISO 27001 and ISO 27018 series of certifications is now a standard requirement for hosters and cloud providers.
ISO 27001 defines a proper information security management system and how information security is handled. ISO 27018 describes how personal data is handled in the cloud. The C5 certification of the German Federal Office for Information Security (BSI) was also implemented specifically for the German region.
The applicable GDPR regulations are complied with by Microsoft at several levels through various measures and are definitely preferable in terms of level to the company's own data center.
It remains to be seen how the discussion at the European level on the Cloud Act and the associated lack of convergence with the GDPR will turn out. There are first rays of hope in the form of a draft law, which must, however, be further examined by the federal states.
If there are concerns about the Cloud Act, we clearly recommend the use of encryption, as mentioned above, to counteract the scenario of U.S. authorities accessing U.S. citizen and corporate data.
This ensures that, in principle, the secure operation of SAP systems on the Azure Cloud is possible. After more than three years of operating SAP and non-SAP systems on Azure, we can say that the Azure platform definitely represents a security and availability gain for customers. Due to the large number of security measures that are standard in the Azure cloud, the level of security is already significantly increased.
The extensive audits and certifications ensure a permanent development of the security and reduce the own costs and allow to use the security budget for innovative IT projects.
Conclusion
After now more than three years of running SAP and non-SAP systems on Azure, we can say that the Azure platform definitely represents a security and availability gain for customers. Due to the large number of security measures that are standard in the Azure cloud, the level of security has already been significantly increased. The extensive audits and certifications ensure permanent further development of security and reduce the company's own costs, making it possible to use the security budget for innovative IT projects.






