Success factor data classification


Classic role-based access concepts are static and initially only describe the user's role abstractly with profiles such as "employee" or "project manager".
Many SAP administrators establish the reference to departments and project groups by defining variants such as "Employee Dept. 1", "Employee Dept. 2" or "Project Manager Project A". In this way, they force organizational dynamics into an inherently static concept that is neither administrable nor effective in the long term.
Limits of the SAP authorization concept
As soon as an employee changes departments or works on several projects at the same time, an enormous maintenance effort is created that is almost impossible for IT departments to manage.
In many cases, the complexity of the profiles even increases to such an extent that no one knows any more which access rights are de facto assigned. The response of IT administrators then often lies in a very restrictive handling of authorizations.
The result: users are impaired in their day-to-day operations and process efficiency suffers. Not infrequently, this leads to a short-term, generous relaxation of individual rights corsets without conducting an in-depth analysis of the security risk.
For the moment, the problem seems to be solved, but due to the high resource commitment in IT departments, the measure is often not reversed and the once secure authorization concept develops into a free pass for insider attacks and data theft.
The increasing digitization and networking of applications is also pushing proven processes to their limits. Both SAP S/4 Hana and numerous connected third-party applications have their own authorization concepts that are not integrated into the traditional SAP authorization system.
The security risks that arise as a result are recognized by many departments, but continuous synchronization often fails due to a lack of budgets and resources: The CISOs (Chief Information Security Officers), who are actually responsible for the topic, usually have no resources of their own and receive little support from operational IT, because the employees are already busy with other projects.
While the CIO still relies on his specialists at this point, the topic of data security ends up on the desks of the CEOs and CFOs, who, however, are far too removed from the topic in terms of content. And yet, in most cases, it is they who are liable when an incident occurs - a Bermuda Triangle that needs to be broken.
Establish data-centric security concepts
In order to be able to effectively secure SAP data in the digitalized world, new types of dynamic IT security concepts are needed that tie in with the SAP authorization concept but place the data itself in the foreground.
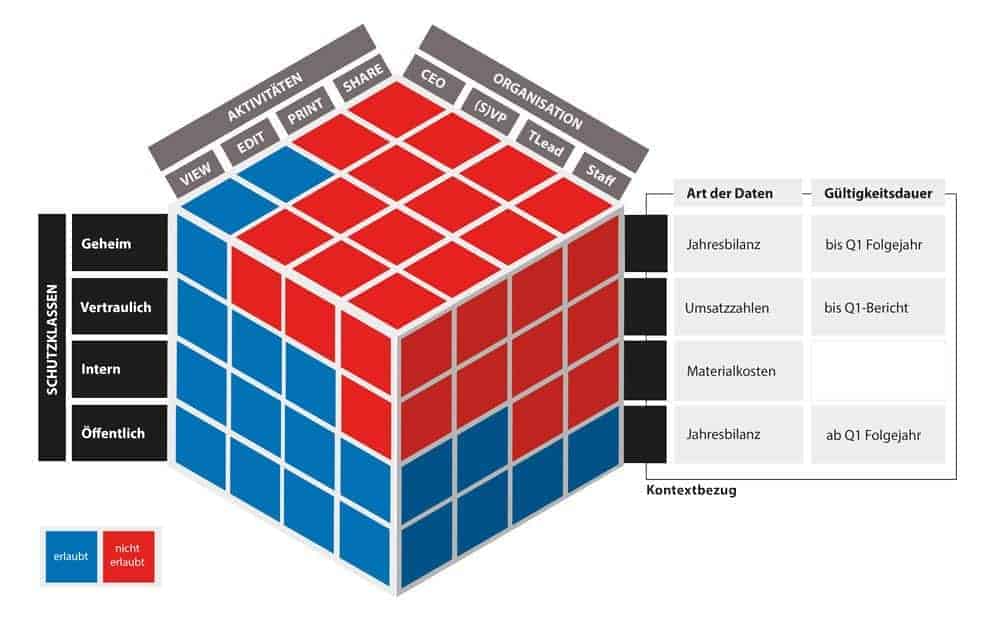
For this purpose, a company-wide standardized data classification is essential. To implement this in the company, those responsible should first focus on the processes. They help to understand, but also to critically question, what the data is needed for and how it is processed.
As soon as these findings are available, the significance for the company's success and the respective protection requirements can be derived. To speed up the process, the use of modern process analysis software is recommended. Afterwards, clearly delimitable data and protection requirement classes should be defined and described.
There are two key challenges to be overcome here: The first concerns the general comprehensibility and comprehensibility of the individual protection requirement classes.
In other words, what does it mean when data is classified as "confidential," for example? Which user groups and roles are allowed to access which data, and to what extent?
Effective data classification must answer these questions in a way that is comprehensible to all users and must not contradict the requirements that arise from the individual process steps.
The second challenge is of a more technical nature and concerns the dynamic or adaptive implementation of the protection requirement. A contextual classification is helpful, in which the organizational and technical environment of the data generation or use is used and automatically compared with the definitions of the protection requirement classes.
This approach has several advantages over the classic, content-based classification: First, it is less dependent on changes that occur, for example, when content or file types are adjusted.
On the other hand, it enables other dimensions to be taken into account, such as the time reference. Financial data or product innovations, for example, lose their confidentiality when they are published.
An effective data security concept is aware of these dynamics and automatically adjusts access rights at the right time. The same applies to organizational structures and hierarchies.
Ideally, during the authorization check, the security solution uses a centrally maintained, digital organization chart to query which hierarchy level the user belongs to and automatically applies the appropriate protection classes.
Secure SAP data across system boundaries
For SAP administrators, the new, data-centric approach means that they must think beyond SAP system boundaries when it comes to security. If data for which SAP is the original and authoritative data source leaves the SAP system through user downloads or background data transfers, it should be classified multidimensionally in any case.
SAP provides a very extensive context of attributes for this purpose, which facilitates an automated implementation of the classification. However, this does not prevent the data from leaving the secure SAP boundaries. Anyone who wants to secure SAP data effectively outside the SAP world needs additional technologies.
This is exactly where Secude's Halocore comes in. Based on contextual data classification, the data security solution controls SAP user downloads and exports. Unauthorized downloads are blocked so that critical or sensitive data does not leave the SAP system in the first place.
Data that is required outside SAP is automatically provided with the corresponding Microsoft AIP/RMS protection profile (Azure Information Protection/Rights Management Service) and encrypted. This transfers the classification and authorization profile from SAP to the exported file.
For the first time, this enables cross-process protection that does not affect either operational IT or users in the business departments. Data security follows the data and is not constantly reinterpreted by the individual application silos.
Conclusion
The core of the implementation of new types of security concepts is a multidimensional, context-related classification of all company data with an increased need for protection. This can be derived from the business processes with the help of automated analyses. A decisive factor in defining the data and protection requirement classes is the clear traceability of which user groups and roles are allowed to access the corresponding data and to what extent.
It must be obvious to the user which data class must be selected when saving the document. Adding the dimensions time and hierarchy can also ensure that the data can be effectively protected in all further SAP-supported process steps.
However, in order to secure the data across application boundaries, additional technical solutions are required that ensure the transfer of the protection requirement outside the SAP systems as well. Cross-application data security solutions that can map data classes in addition to user roles are recommended here.
In any case, one should rely on established standard platforms that are supported by all common applications as a "security instance". For example, Halocore uses Microsoft standard technologies to enable required data exports beyond SAP's
Protect borders.
[/av_promobox]








