The Privacy Problem with Blockchain


Data in a blockchain network is first of all never private but can be read by other members of the network. This fundamental problem can, however, be overcome with Trusted Computing Appliances.
There are use cases where trustworthy processing of private data is not possible with current blockchains. This is very problematic especially when intellectual property needs to be protected at the same time as accelerating existing manual processes involving experts and legal advisors. Examples of such processes are the communication of regulated food additives in the consumer goods industry or substance control within the framework of drug approval. But why can blockchains not be used for trustworthy processing of private data today? After all, “trustworthiness” tops the list of this technology’s advantages. The crux of the matter concerns the nature of “private” in the data to be processed.
In a classical sense, data in a blockchain is never private, i.e. it can always be read by other members in the network. If data is encrypted before being transmitted to a blockchain, it cannot then be processed by means of smart contracts unless the smart contract in turn decoded it. But then of course the necessary decoding key would be visible to all members. The Hyperledger technology is attempting to solve the visibility problem using so-called “channels” that certain members of a blockchain network can share. Depending on the complexity of the network of relationships, this approach can, however, very quickly become unmanageable and uneconomical. And it is precisely in manufacturing industries that very heavily protected intellectual property is to be found that may never leave the corporate network—and certainly not towards a decentralized system over which the owner doesn’t have complete control. Camelot ITLab’s Trusted Computing Appliances offers one possible solution to the privacy problem.
Additional services Trusted Computing Appliances
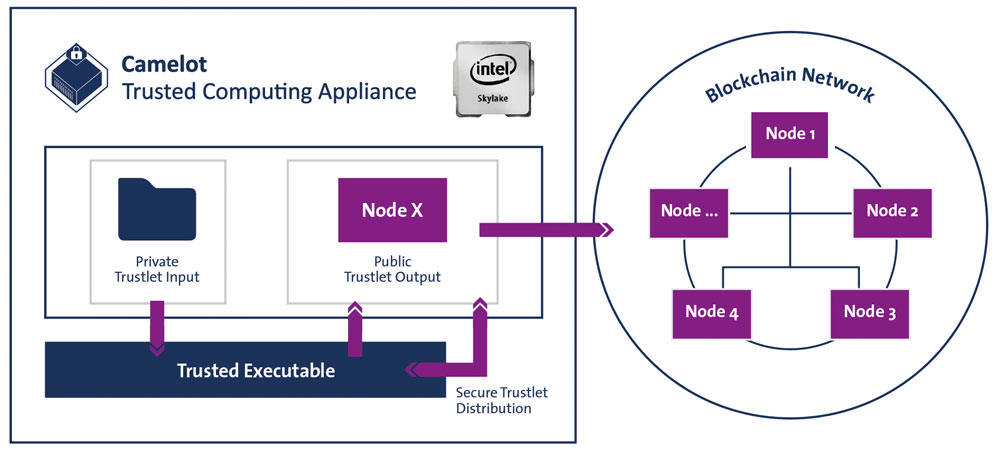
The concept works as follows: an owner’s private data is saved only locally but registered via hash value on the blockchain. This eliminates the possibility of the owner ever manipulating the data in his own favor at any time. All the parties agree on an algorithm (program) that is allowed to process the private data, for example a simple cross-check between two lists as well as the return of the intersection. Ideally, the distribution of the program between the parties connected to the network is also done via blockchain mechanisms. After executing the program, the returning value (intersection) may be distributed via the blockchain to the corresponding remote nodes. But this approach has the following drawback: Since the program runs on the infrastructure—the PC or server—of the data owner, this person could manipulate the data himself and thus falsify or distort in his own favor the returning value reaching the blockchain. This is where Trusted Computing comes into play.
Using measures firmly anchored in the processor, it prevents manipulation of local programs as well as any interference in the running processes of this program. The Trusted Computing Appliance thus facilitates the operation of “Off-Chain Smart Contracts” which although local, still run in a trustworthy environment. Camelot calls these above-mentioned programs, which all members of the network agree on, “trustlets”; the trustworthy environment in the current service version is Intel SGX (Software Guard Extension). The biggest challenge when developing the Trusted Computing Services was to render secure the unsecured area between the blockchain and the trustlets. This was achieved with the aid of a coherent concept that describes onboarding mechanisms which function using voting machines and data integrity achieved through digital signatures, the blockchain to be used being in principle freely selectable. Camelot’s reference implementation uses Hyperledger Fabric in the SAP Cloud Platform Blockchain Service.
Besides processing protected data, the technical use cases also comprise for example what is known as the inter-blockchain transfer of data, i.e. safe transfer of transactions from one blockchain technology to another as well as inserting data from secure data sources into a blockchain network. Trustlets relate exclusively to code compiled by Camelot. However, also script language interpreters are planned for the next version of Trusted Computing so that the algorithms can be distributed in real time. This shows that this field still has a high optimization and development potential badly needed in the marketplace.
To the partner entry:

PDF Download in English: