A new understanding of security


According to a report in Der Spiegel on March 7 of this year, a special situation report by the German Federal Office for Information Security (BSI) warns the German government that Germany could soon face an attack against "high-value targets" in connection with the Russian invasion of Ukraine: Since the beginning of the crisis, one can see "Cyber attacks, for example, against energy suppliers or military facilities in security circles as the greatest current threat to Germany."
The German Federal Office for the Protection of the Constitution warns that Russian intelligence services have the capability to "significantly and sustainably sabotage" critical infrastructure. Yet this development is not new: The AXA Future Risks Report 2021 already identifies the risks posed by cyberattacks as the second most important global threat after climate change and ahead of pandemics.
Kritis architectures
No one wants to imagine the consequences of a successful hack for a nuclear power plant or waterworks. Or even if attackers succeeded in shutting down power across the board. Critical infrastructures affect many areas of daily life. In addition to government and administration, energy and water, they also include health, food, transportation and traffic, finance and insurance, information technology and telecommunications, media and culture. Their threat situation is addressed by the new IT security law SiG 2.0, which came into force at the beginning of the year.
The Security Act requires procedural, directive and reactive measures, including security monitoring in systems, monitoring measures to harden systems in advance to market standards. And there are specific requirements on how to build kritis architectures. It is mandatory to define the infrastructure and processes in such a way that they can later be audited and accepted with regard to SiG 2.0. This quality of the architecture and the processes must be proven every two years and requires a change in thinking: You cannot simply continue to do what you have always done, but must fulfill specific requirements.
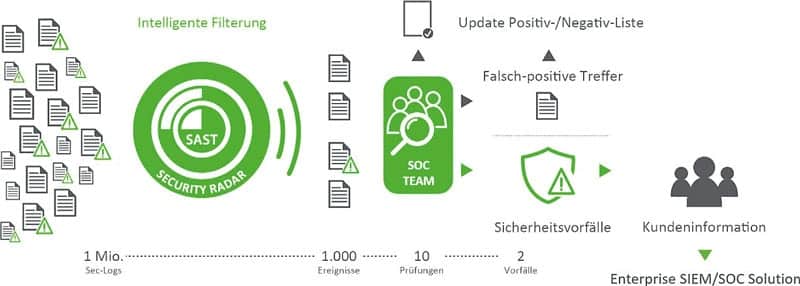
An important point of the security law is: responsibility has been redefined and monitoring and control mechanisms must be integrated and now evaluable in real time. This corresponds to our experience of the last few years: Most were operated purely functionally and had no sensor technology with which we could have been detected in any way, for example, during commissioned penetration tests. And if we succeed in doing this during the agreed penetration test, a real attacker will also succeed.
This means that until now, companies have usually only been able to identify their deficits once a serious security incident had already occurred - and it remained unclear how long this vulnerability had already been exploited. In addition to the general reporting office for IT security at the national level, the BSI should therefore logically now also be allowed to detect security risks. The so-called hacker paragraph allows the BSI to "attack" companies and infrastructures in order to subsequently demand the implementation of technical and organizational measures. The intention is clear: malware, security vulnerabilities and risks are to be proactively found and eliminated.
SAP example
The example of SAP system landscapes shows that the requirements of SiG 2.0 are a step in the right direction, even for non-critical companies, but naturally cannot cover all weak points. For S/4, for example, the requirements have changed once again; the database, user interface, gateway, applications and authorizations have grown closer together, and access to important data has become more complex - and thus more difficult to monitor. SiG 2.0 requires detailed business continuity planning and disaster recovery scenarios with the use of intrusion detection systems (IDS) according to the "state of the art" (§8a).
IDS detect and substantiate attacks with the help of log files, which must now not only be recorded, but also evaluated. This means that SIEM systems will be indispensable for the rapid identification of cyberattacks in the future, even if they are often not sufficient for SAP. This is because they primarily look at infrastructures, and here SAP, as a largely independent system, falls through the detection cracks unless the expertise of SAP security professionals and special software are used.
Through its integration with the SIEM tool, all security-related incidents of SAP landscapes can be consolidated with other relevant IT systems and the integrated dashboard additionally creates transparency across all systems. Critical enterprises and anyone with a realistic need for security thus receive an assessed dashboard-based representation and documentation of their entire security status at the push of a button. In the case of SAP, the involvement of a professional security partner is therefore essential for the immediate implementation of SiG 2.0.
In this way, the existing SAP customer rku-it, as an IT service provider for energy suppliers, not only effectively fulfilled the requirements of the new IT security law 2.0, but at the same time increased the revision security of the SAP system landscape. By using the Sast Suite, derivations of the template roles could be realized depending on the customer's organization. In operation, it is used to validate the roles and authorizations for security and SoD, for usage analysis, further optimization of roles and authorizations, and for the use of emergency user functionality for support tasks of rku-it employees.
Problem areas and opportunities
A serious problem for a holistic safety strategy oriented to SiG 2.0 is still the lack of focus. Management must address this issue with the urgency and prioritization that is now required, and consequently also focus and make resources available. This requires attention, personnel and, of course, money. But it can still be observed in many companies that the formation of positions, departments, staff units is often still so stepmotherly even in an organization that is concerned with availability and security, as if this were optional. However, due to current developments, this formation and availability must simply be considered a requirement, not only for Kritis operators, and first costs top-down investment.
SiG 2.0 and Conversion
To return to the example of SAP: An upcoming S/4 migration in particular can also be used as an opportunity to raise the company's own IT security to a new level from the perspective of SiG 2.0. It provides an opportunity, for example, to clean up the old interfaces and, above all, to standardize them. Critical operators such as utilities would be a classic case here. There are very long process chains, metering points, metering point operators, billing, the separation of sales and network. Very complex systems, where you also look at the business is highly standardized by regulatory requirements, software, processes - and these are things that you can scale very well, where you can form good templates for energy, gas and water, harmonize the interfaces and then introduce the templates for authorizations, users and processes. It's a huge security gain when you standardize things so that they work the same way and processes run the same way.
Security Competence
Ralf Kempf and his team work for around 200 customers in the SAP Cyber Security and Access Governance environment, including many Kritis operators: "We know the challenges that Kritis operators now face and support them in effectively meeting the requirements of SiG 2.0 while increasing the security of their SAP system landscape. So the days when companies could afford to treat their IT security stepmotherly are definitely over - and that doesn't just apply to Kritis operators. It is therefore crucial to have a holistic security approach and strategy that combines all the issues and takes account of the current threat scenarios.





