Bring Your Own Key


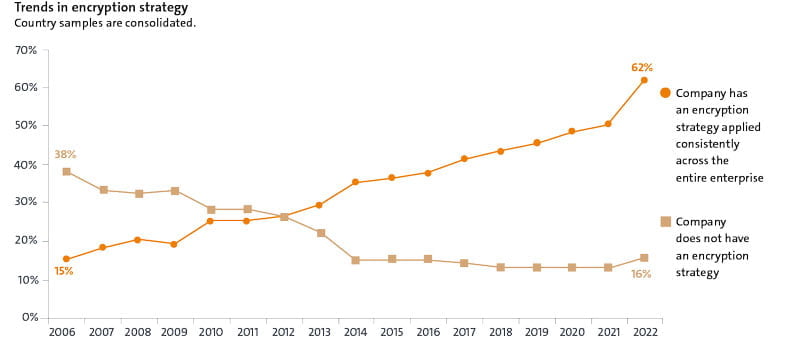
A survey already shows a steady increase in the use of enterprise-wide encryption over the past few years. This year, however, there was a dramatic jump: The percentage of IT professionals whose company has a consistently applied encryption policy increased from 50 percent to 62 percent! Similarly, 61 percent of respondents welcomed their executives' support on encryption. These and other findings emerged from the latest Entrust Global Encryption Trends Study, now in its 17th year. The study analyzes the various challenges and measures taken by companies in the fight against cybersecurity threats. For this purpose, security and IT experts from various nations are surveyed once a year.
Encryption strategies
Another positive finding of the report is reduced difficulty in implementing encryption strategies, particularly in locating and classifying data. The findings clearly demonstrate that companies have not only recognized the security issues, but have also addressed them. But they also reveal gaps in the implementation of encryption solutions within certain sensitive categories. For example, only 34 percent of respondents in each case say they comprehensively encrypt data containers or IoP platforms, and only 31 percent for Big Data repositories. The situation is similar with hardware security modules (HSMs). While 63 percent of all respondents worldwide rate these as an important part of an encryption and key management strategy, half say they do not yet have HSMs.
This year's study also shows how the distribution of sensitive data across multiple cloud environments is forcing organizations to increase security in this area. This is especially true for containerized applications, where the use of HSMs is at an all-time high of 40 percent. More than half of respondents (55 percent) admit that their organization transfers sensitive or confidential data to the cloud - whether or not it is encrypted or made unreadable through some other mechanism such as tokenization or data masking. However, another 27 percent say they will do so in the next one to two years.
Ransomware
"The proliferation of multi-cloud environments, containers and serverless deployments, and IoT platforms is creating new security challenges for many enterprises", explains John Metzger, vice president at Entrust. "This is exacerbated by the rise of ransomware and other cybersecurity threats. Companies are responding by trying to retain control of encrypted data themselves - rather than leaving its security solely to platform providers."
When it comes to protecting their data at rest in the cloud, 44 percent of IT professionals (up from 36 percent in 2021) say encryption is done in the cloud first - with keys generated and managed by the cloud provider. Another 38 percent say their data is already encrypted before it is sent to the cloud - with keys generated and managed by their own company. Another 21 percent use some form of Bring Your Own Key (BYOK).
In summary, these results illustrate once again that the benefits of cloud computing outweigh the risks associated with transferring confidential data to the cloud. They also illustrate that encryption and data protection in the cloud are now preferentially handled directly by companies. In terms of sources of risk, security officers cite employee mistakes as the biggest threat that could lead to sensitive data being exposed - although the number is down slightly from last year, while the perceived risk from temporary or contract workers is at its highest level ever.
In addition, system or process malfunctions and hackers are named as particularly critical. Threats to sensitive data come from all directions. It is therefore not surprising that almost three quarters of all respondents admit that their companies have suffered at least one data breach to date. Just under half have even been affected in the past twelve months.






